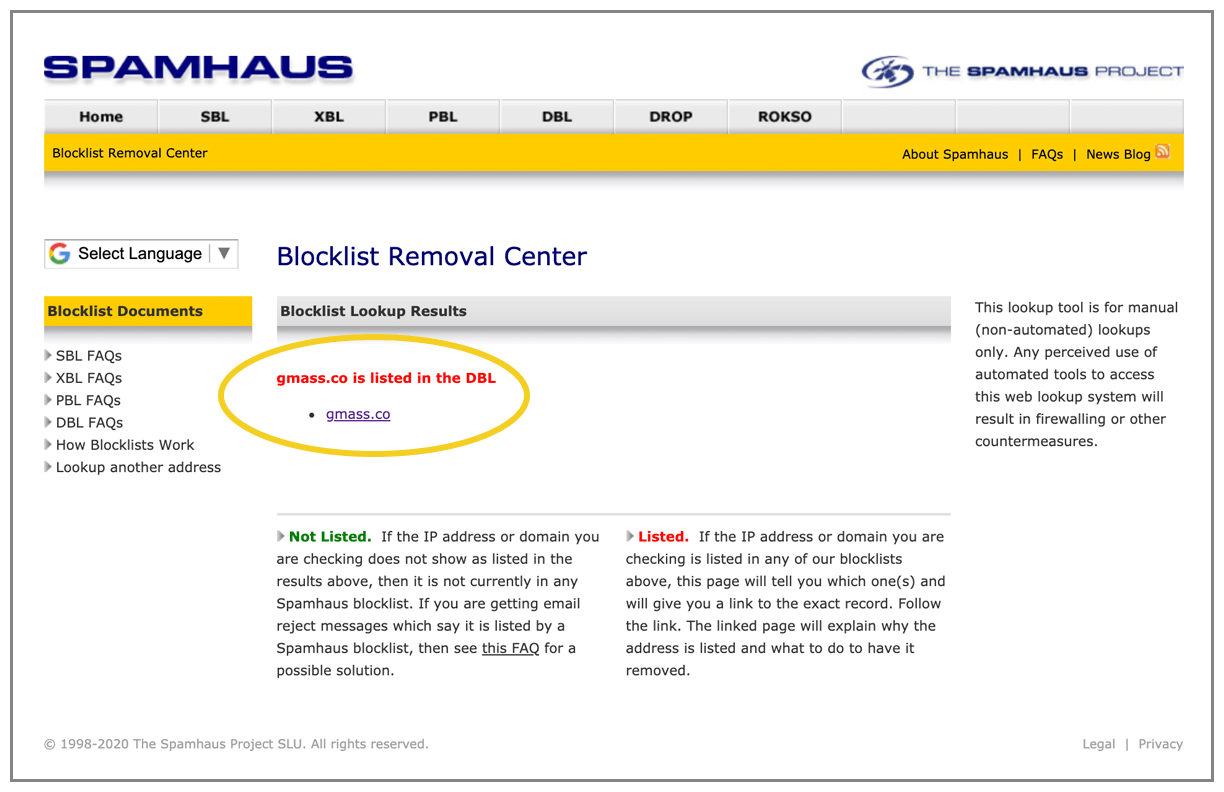
About a month ago, our primary domain, gmass.co, was added to the Spamhaus Domain Blocklist, a.k.a the DBL. The Spamhaus Project operates the world’s most widely used blacklists that are used to filter email and other Internet traffic. Spamhaus can’t block any traffic itself. They just publish IPs and domains from which they recommend that others block traffic. Their power is derived from the sheer number of organizations that have opted to use their lists of IP addresses and domains names to filter email. Microsoft, for example, uses the Spamhaus SBL list of IP addresses to block email to consumer email accounts @live.com and corporate accounts hosted on Office 365. While Spamhaus does provide explanations for listing IP addresses on their SBL list, they do not provide explanations for listing domains on their DBL list, but based on the evidence, I’m fairly certain a Spamhaus admin saw the GMass website, decided they didn’t like it, and then added my domain to the blocklist. More on that later.
The implications of being on the DBL are far and wide, and as I’ve discovered, the consequences go far beyond just having email blocked. In fact, I discovered that big companies like Twitter and LinkedIn use the Spamhaus DBL in ways about which most people are completely unaware. The exact return code for gmass.co is 127.0.1.2, which means Spamhaus has categorized it as a “spam domain.”
But it’s not. And Spamhaus won’t tell us why they’ve put gmass.co on their list. So read on.
What happened, exactly?
In early August, GMass released a new feature, the Email Verifier. It’s similar to commercial email verification services like NeverBounce and ZeroBounce, but ours was a free service. Our email verifier worked by establishing an SMTP connection and analyzing the response after the RCPT TO command. This is sometimes known as the “broken handshake” method of verifying an email address. Other platforms, whose sole business is email address verification, use this technique plus other techniques to validate an address.
Shortly after I launched the verifier, the four IP addresses I was using to conduct verifications became listed on the Spamhaus CSS list, which is an automated list of IP addresses that are engaged in “sending low reputation email” or represent “compromised hosts.” The CSS list has a self-removal delisting process, which I used to delist the IPs, because I was confident that I wasn’t violating any of the rules, and I figured that the listings were simply due to high SMTP traffic originating from IPs that had never had any SMTP traffic before.
Also, I soon consolidated the verifier so that all verifications originated from a single IP rather than multiple ones.
Eventually, the CSS self-removal process stopped working, so I reached out and asked for the IP address to be manually removed. My request was denied.
Here’s the interesting part. My logs show that my domain, gmass.co, was added to the DBL within ten minutes of a Spamhaus admin responding to my request for the delisting of my IP from the CSS list.
GMass.co has been a registered domain for more than five years, and GMass has offered the same service (sending campaigns through Gmail) for all five of those years, but inside a ten-minute window of a Spamhaus admin responding to my IP delisting request, the GMass.co domain was added. The only way that could have happened is if in denying my IP delisting request, the admin thought:
“Well, gee, not only am I going to deny your IP delisting request, but I’m also going to add your entire domain to the DBL.”
The DBL documentation states: “Most DBL listings occur automatically, although where necessary Spamhaus researchers will add or remove listings manually.”
Based on the timing of events, it sure seems like Spamhaus targeted GMass and added my domain manually.
The immediate consequences of a DBL listing
The Spamhaus DBL is used in ways I could never imagine. The intent of the DBL is to allow email server admins the ability to filter out email that contains spammy domains, and the DBL admins are the arbiters of decisions about whether a domain is spammy or not. What I found, however, is that the DBL’s reach goes far beyond email.
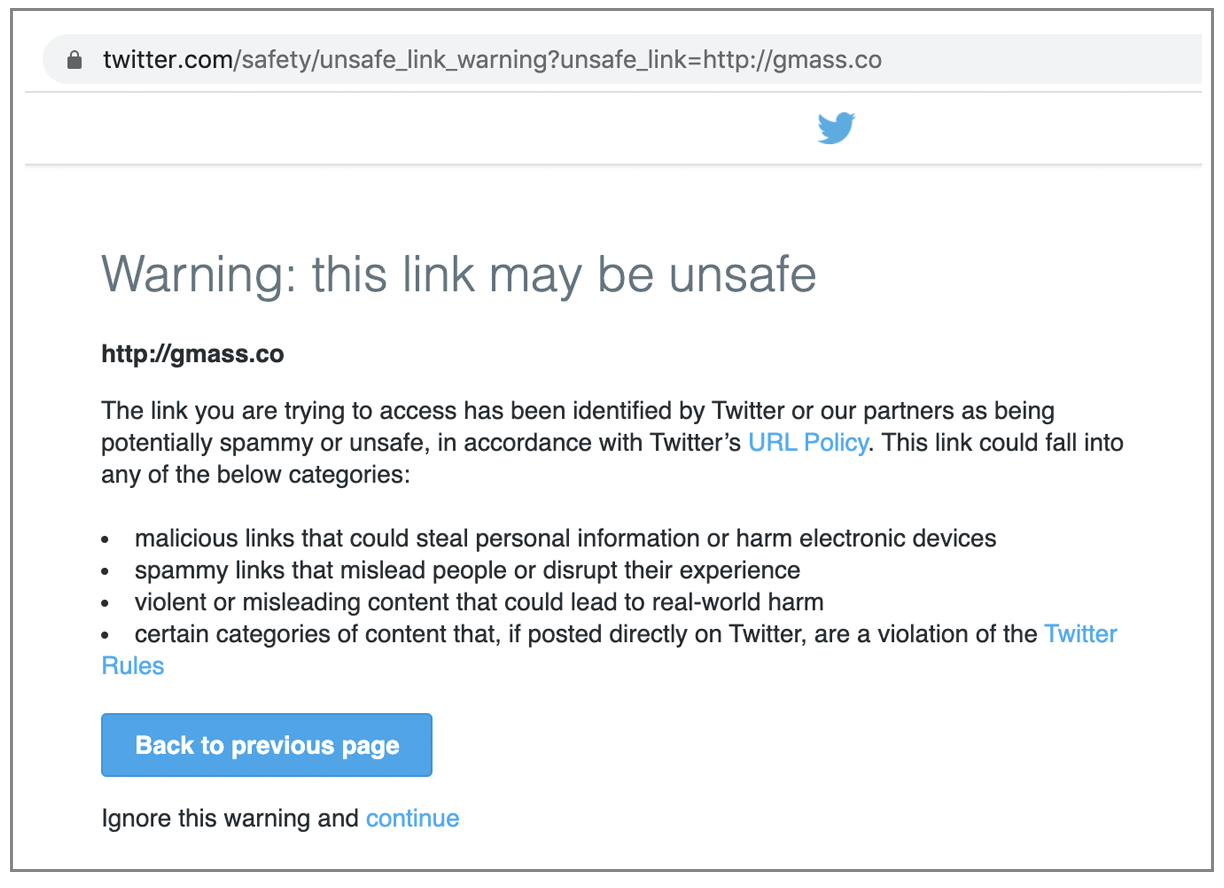
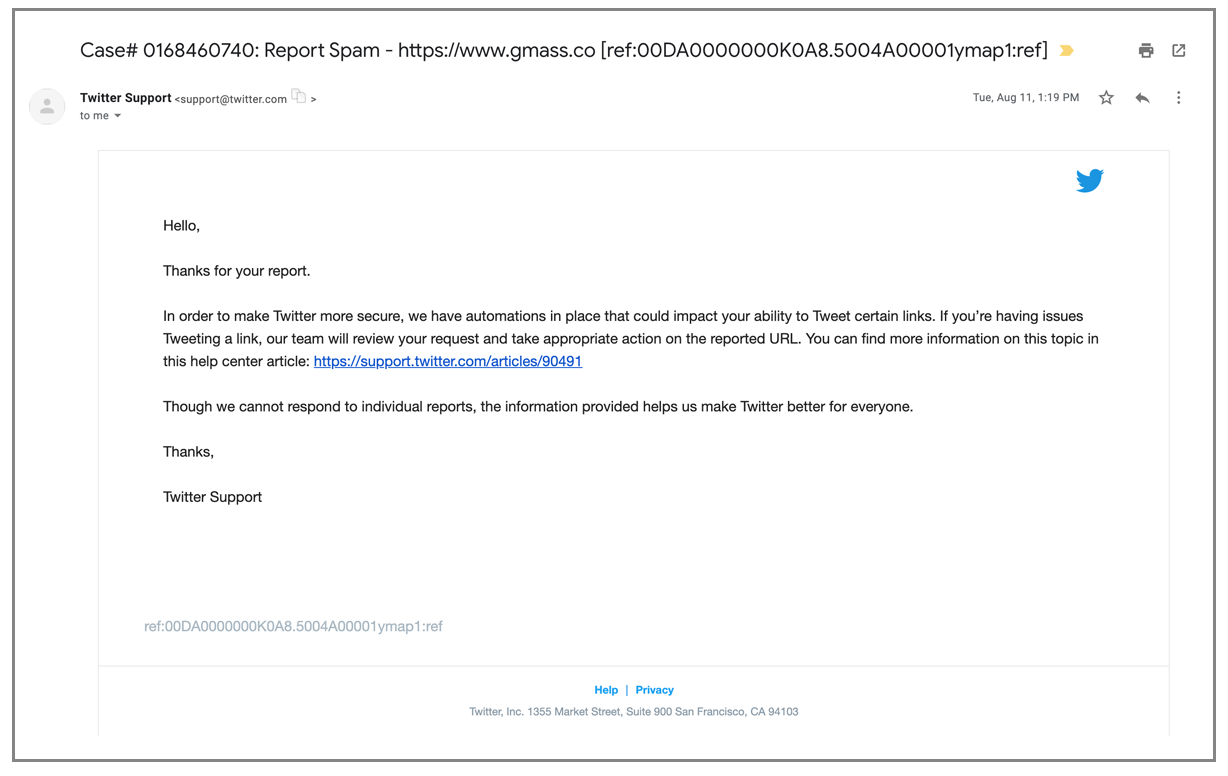
All links to gmass.co on Twitter stopped functioning. They began to be redirected to a Twitter interstitial page that warned users that the URL is unsafe and recommended they don’t proceed. Here’s what people saw if they clicked a link to gmass.co in any tweet:
Even the link to gmass.co in my Twitter bio would send users to this “Unsafe URL” page.
At first, I thought Twitter itself blocked gmass.co since I discovered the Twitter issue before I was even aware it was added to the Spamhaus DBL. But then I tested this by tweeting links to other domains that are listed on the DBL, and the same thing happened.
So, Twitter uses the Spamhaus DBL to mark links as unsafe.
I figured I might get around this by using a URL shortener. So I went to tinyurl.com and created a shortened link to the GMass homepage and used that in my Twitter bio. Didn’t work! Twitter was smart enough to check the redirect of a URL, and if the redirect went to a domain on the DBL, it was also blocked. Wow!
This story has a happy ending though. I reported the issue to Twitter using their spam help form.
Several weeks later, I noticed that links to gmass.co started working again. Other than this auto-response after filling out the form, I never heard anything directly from them, even after they cleared the block on gmass.co.
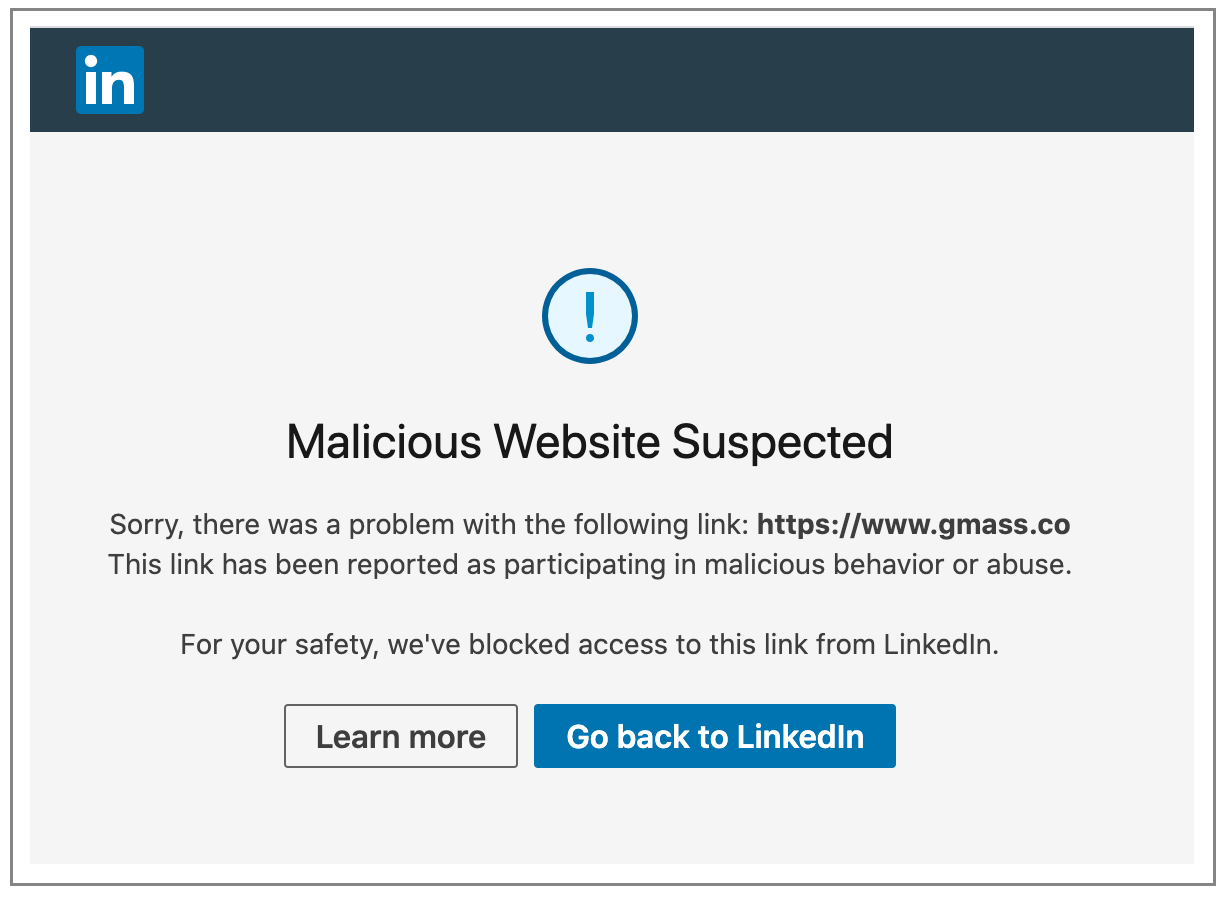
Similar to Twitter, LinkedIn also blocks links to a domain listed on the DBL. So on the GMass company page, if the domain is shown as gmass.co, this is what you see if you click:
Unlike Twitter, however, LinkedIn does not check for redirects. With LinkedIn, a tinyurl.com shortened link that redirects to gmass.co would still work.
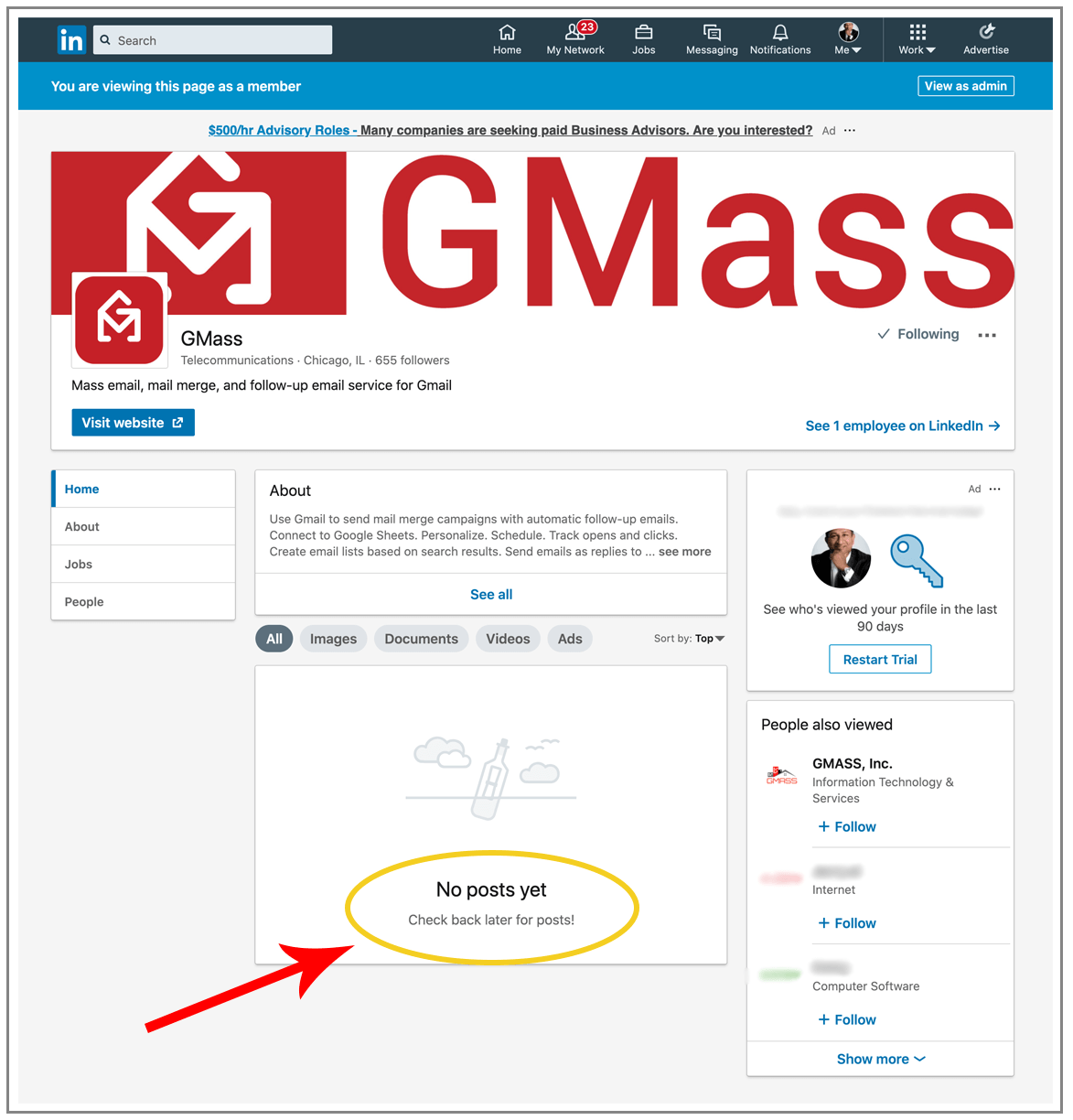
LinkedIn, however, does go one step further than Twitter by blocking all the content on any company page if that company’s main domain is on the DBL.
Wait, all my posts are gone!
I should put the thumbs-up “like” icon right here, because no links to gmass.co on Facebook were blocked. I applaud Facebook for making their own decisions about domains rather than using Spamhaus.
The entire country of Norway
This was the most unexpected consequence. A Norwegian GMass user contacted me to tell me that he could no longer use the GMass website, and the extension inside Gmail wasn’t working either. Turns out that Norway’s largest ISP, Telenor, uses the Spamhaus DBL to block people from even accessing the website if its domain is on the DBL.
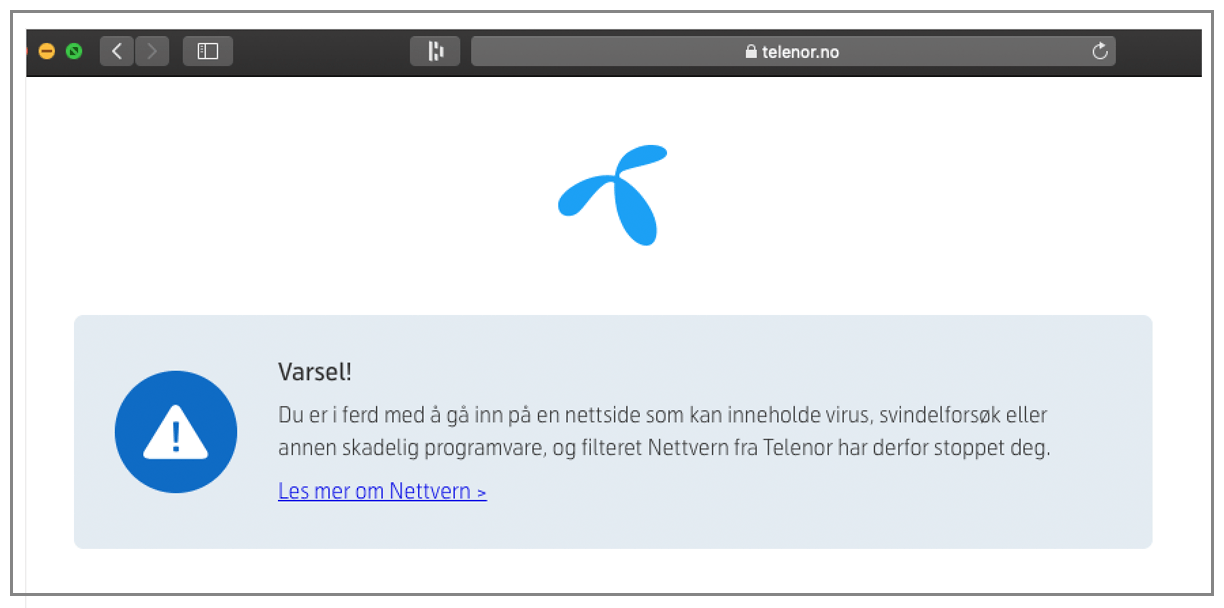
Since our Chrome extension’s API endpoints are all gmass.co URLs, the connections to the endpoints stopped working also.
I tweeted Telenor asking them to stop doing this, but not surprisingly, they didn’t respond.
@TelenorGroup A mutual user of mine and yours told me that you block users’ access to domains on the Spamhaus DBL. Can you reconsider this decision? It’s silly to block access to a website because Spamhaus thinks the domain is involved in spam. Email and web are different.
— Ajay Goel (@PartTimeSnob) August 19, 2020
What about actual email?
Since the main point of the DBL is to block email containing listed domains, you might think that a lot of GMass email was blocked as a result of the DBL, but you would be wrong. That’s because the gmass.co domain rarely appears in email. It only appears in transactional notifications that we send to our own users, such as when they sign up for an account (“thank you” email), or when a campaign finishes sending (“your task is complete” email). But even when we do that, we don’t technically email our users. We “insert” the message directly into their Gmail inbox, bypassing the SMTP protocol entirely. And for our corporate communications, we use the wordzen.com domain since GMass was originally a service of its parent company Wordzen, Inc. (The name of the company has since been changed to GMass, Inc. but we left our old email addresses intact.)
So, we can conclude that by Spamhaus listing the gmass.co domain in the DBL, it stopped exactly ZERO additional spam worldwide.
Spamhaus returns the code 127.0.0.2 for gmass.co, which means it’s a “spam domain,” according to this page. But what does that even mean? Does it mean that they’ve found gmass.co in actual spam? I’d like to see examples, because if that’s the case, it certainly wasn’t sent by us. Does it mean that gmass.co has been designated a spammy organization? (How can we be spammy if we’re not sending many emails?) Does it mean that gmass.co hosts content promoted by spammers? (It doesn’t; gmass.co doesn’t host any user content.)
Spamhaus provides no explanation.
Diving into URL shorteners
Spamhaus recommends that sysadmins of URL shortening services use the DBL to prevent redirects to listed domains. On the DBL FAQ, they state:
“URL shortening services should check every URL’s domain against the DBL and not allow those that are listed.”
This is interesting because a) Spamhaus is admitting that the DBL should be used for purposes beyond email filtering, and b) because apart from my findings with Twitter and LinkedIn above, no regular URL shortening service uses the DBL to prevent redirects. What I mean by a “regular” URL shortener is one that isn’t controlled by a social media company… i.e., one that anyone can use to shorten a URL without the URL having to appear in a tweet or a post. Popular URL shorteners include TinyURL, bit.ly and a relatively new arrival on the market, t.ly. I tried creating shortened URLs to gmass.co with all of these services, and thankfully, they all work. (You can try too by clicking the links I just provided.)
I applaud each of these services for weeding out abuse on their own and not relying on the Spamhaus DBL.
Addressing the elephant in the room: is GMass a spammer?
The DBL policy does state that Spamhaus admins can add domains as they see fit. My guess is that an admin saw the GMass website, decided that GMass is a spam operation, and added our domain to the list. That begs the question: Is GMass a spam operation? Obviously, I don’t think so, but why don’t you decide for yourself?
Here are some facts to consider:
- GMass doesn’t actually send any email. All of our users’ email campaigns are sent natively through their Gmail accounts or through a third-party SMTP service. The IPs that send the email don’t belong to GMass. They belong to either Google or an SMTP service like SendGrid or Amazon SES.
- Because GMass doesn’t send any mail through its own IPs, spammers are terminated by the companies whose IPs are being used. If a spammer sends spam using GMass, and is sending natively through Gmail, then Gmail will terminate the account. If the spammer is using GMass to send through SendGrid, then SendGrid will terminate the account. While some spam does occasionally get sent by a GMass user, as it can through many other email service providers, most spammers are eventually terminated by the network that actually sends the spam.
- GMass employs two full-time security staff who monitor campaign sending activity almost 24 hours a day, 7 days a week (there are a few gap hours in there, but it’s almost constant). This team analyzes emails for phishing/scammy/illegal content and terminates accounts within minutes.
- GMass can be used to send cold email, and many of my industry colleagues classify any cold email as spam. Spamhaus defines spam as email that is both “sent in bulk” and “unsolicited.” Cold email is definitely unsolicited, but if it’s highly personalized, then it is not “sent in bulk.” Ultimately, what’s the difference between typing out 30 individual emails and pressing “send” 30 times, versus using automation software to help you do that?
- Even if you decide GMass is a spam operation, and gmass.co should be listed on the DBL, then so should hundreds of other domains like mailshake.com, yesware.com, mixmax.com, woodpecker.io, lemlist.com… I could go on. What do they all have in common? They’re all email service providers that integrate with Gmail.
- Spamhaus obviously doesn’t like something about gmass.co. Here’s a list of other domain blacklists that don’t have any issue with gmass.co at all: URIBL, SURBL, Barracuda, VirusTotal, Invaluement.
So then, why did Spamhaus target GMass but none of its competitors? First, they had to become aware of GMass, and by our asking for their help with an unrelated IP delisting request, they became aware. Or perhaps it goes deeper than that. GMass has created controversy in the past. We are the only email service provider to offer a completely free email verification service, and maybe Spamhaus didn’t like that. We invented a technique to prevent pixel blockers from stopping open tracking on campaigns, and perhaps Spamhaus found that practice objectionable. We’ve built a lot of interesting features and technology over the years. We’ve generated controversy. Maybe one feature pushed GMass over the edge and into a “spam operation” classification in the eyes of Spamhaus.
Are GMass users affected?
No. If you use GMass to send email campaigns, you aren’t affected by this issue, because the gmass.co domain does not appear in your email campaigns. The domains that appear in your email message include:
- Your organization’s domain, if you’re sending “from” your organization’s email domain.
- If you’re sending from a @gmail.com account, then “gmail.com” is present, not gmass.co.
- If you have open tracking turned on, then your tracking domain is present.
- If you have links present, and you don’t have click tracking ON, then the domains in your links are present. Or, if you do have click tracking ON, but your links have anchor text that is a URL rather than a phrase (which bypasses click tracking functionality), then those domains will also be present.
The danger of the growing power of the DBL
I’ve shown that being listed on the DBL doesn’t just impact email delivery. It impacts social media links, and even the ability for some people to access a website listed on the DBL. Imagine, though, if the DBL were able to expand its influence to Google search results, the Google Safe Browsing program, or Facebook. The impact of large social media companies and search engines using the DBL blindly as a domain reputation service without any thought to the consequences for innocent users is frightening and dangerous.
What if Google started penalizing domains in SERPs based on being listed on the DBL?
What if the Safe Browsing program using DBL listings to influence whether a user should be able to access a site, similar to what Telenor is doing?
What if cloud hosting services like AWS and Azure started terminating customers whose domains are listed on the DBL?
These consequences would be catastrophic for the owner of a domain listed on the DBL, especially when there’s no explanation and no recourse for delisting.
The benefits of a DBL listing
Benefits?! I’ve always believed that for every seemingly negative circumstance, the universe creates an exactly equal set of positive circumstances. So what’s the benefit? I’ve always been a data junkie. I love collecting and analyzing and even publishing data, like our domain deliverability tool. In this case, being listed on the DBL, and having my verification IPs listed on the SBL, allowed me to collect a treasure trove of data about which domains use each of the DBL and SBL lists. How can I use this list? First, now that I’m aware of the DBL’s footprint, I can reach out to these organizations and ask them to stop using the DBL (see “the path forward” below). Secondly, I can also be sure to delete my signature block (it contains gmass.co) whenever I’m emailing someone at one of these domains.
The path forward
I don’t know if gmass.co’s listing is permanent or temporary. A lawsuit was filed against Spamhaus by a company called DatabaseUSA recently because their domain was listed on the DBL, and the lawsuit sought an explanation for the listing and requirements for delisting. Because Spamhaus is based in the tiny country of Andorra, they don’t respond to US-based lawsuits, so the judge granted DatabaseUSA a default victory. I was curious if Spamhaus would do anything differently afterward. While the listing of the domain remained on the DBL for months after the lawsuit was decided, sometime around the first week of September, I noticed that their domain disappeared from the DBL. Whether that was the result of the lawsuit or just the domain “aging out” of the list, I don’t know; but if it was age-related, perhaps there’s hope yet for gmass.co.
The natural response for any domain owner whose domain is suddenly listed would be to work around the listing. Perhaps change the domain used in corporate email communication. Perhaps avoid using the email in transactional email. Perhaps changing domains altogether and hoping Spamhaus doesn’t notice.
We aren’t changing much. Although we are going to change the URL endpoints of our Chrome extension so that Norwegian users can still use our software, mostly we’re just asking companies to stop using the DBL. We’ve already seen some success by getting Twitter to punch a hole in their blocklist for gmass.co, and we intend to keep pursuing that effort slowly. If you’d like to help with that effort, please get in touch. Or, if you have your own Spamhaus listing story to share, please comment below, and I’ll get in touch.
Send incredible emails & automations and avoid the spam folder — all in one powerful but easy-to-learn tool
TRY GMASS FOR FREE
Download Chrome extension - 30 second install!
No credit card required











I went to your twitter and clicked on gmass.co/g/support and twitter is still showing the “Warning: this link may be unsafe”
Yes, that’s the result of the DBL listing.
You must have friends at Google at this point, right? I would say get Google on your side for stopping the overuse of Spamhaus. It’s basically more powerful than most nation-states. No one wants to be enemies with Google.
I really appreciate what you’re doing. I’ve learned some useful stuff from you.
I wish. I have some contacts at Google, but I wouldn’t consider them friends, and I don’t think they could help in this situation. I’m fairly certain (95%) that Google doesn’t use the Spamhaus lists to filter mail. In fact, I even saw a tweet recently from Spamhaus that says they’re protecting 70% of mailboxes in the world. They’re in bed with Microsoft for sure. If they had a relationship with Google too, they’d be claiming 99%.
We are also on the DBL, with dodgy explanations from Spamhaus.
You mentioned that you don’t send emails from gmass.co. Did you consider removing your MX records? If Spamhaus is supposed to be about email, does this take the domain out of their purview?
I’m happy to send my emails from Gmail. I just don’t want our site incurring the collateral damage of others (mis)using something that was supposed to be about EMAIL…
Hello!
Can you tell me when a domain is automatically excluded from the list of Spamhaus DBL databese?
Spamhaus now it behaves like a terrorist organization that has taken my domain name and business hostage. The domain name registrar has already sent a letter threatening to block the domain, and the Spamhaus does not want to unblock it manually.
I’m not sure what you mean about “automatic exclusion”, but regarding domain name registrars, see my comment below about Namecheap.
“We enable our customers to send spam, using techniques identical to spammers. Why are we marked as spammers? It’s so unfair! It must be personal.”
Do you have any clue what you’re talking about or do you just like to hear your keyboard go clickity-clack?
If it wasn’t targeted, every email platform that integrates with Gmail and allows users to send mail merge campaigns would be on the DBL. We are a low volume provider, and we still take measures to stop obvious spam, including employing 2 fulltime abuse personnel who stop campaigns and terminate accounts all day long. I’m fairly certain out of all the Gmail mail merge plugins, we’re the only ones who even go to that length.
They are mafia. big time bully. need to figure out taking them.
My domain was blacklisted in Spamhaus DBL for “unsolicited email activity” the day it was registered, without any hosting or email service. Namecheap gave me 72 hours to get it delisted. Spamhaus refused to remove it from DBL (without giving any explanation) and now my domain is locked. Spamhaus and Namecheap are holding my domain hostage. The kind of thing terrorists and bullies do.
Namecheap is a particularly terrible domain registrar. Don’t ever register a domain name that’s important to you with them. Here’s some communication from them regarding a domain that was temporarily listed on SURBL last year:
https://dl.dropboxusercontent.com/s/rqiyo209rr9hzui/chrome_HwciHyEDCN.png
They claim that they have to protect their own reputation so domains that are blacklisted are suspended. But then at the same time, they won’t let you transfer the domain out to a different registrar. So they end up holding your domain hostage. Of course, their claim about protecting their reputation is nonsense; otherwise they’d be HAPPY to have you transfer your name to another registrar. So again, avoid Namecheap for domain registrations. I’ve had good experiences with Hover and SAV.